Comprehensive Data Center Security for the Cloud. With TIMi, companies can capitalize on their corporate data to develop new ideas and make critical business decisions faster and easier than ever before. Adabas & Natural has been there for you for decades. Immuta is the market leader in secure Data Access, providing data teams one universal platform to control access to analytical data sets in the cloud. Site Terms and Privacy Policy, Database and Application Security, Reporting and Audit Solutions. Simply replace the data store URL. Click URL instructions: Each year, information stored inthe cloud increases by36%. Single Connect, which enables IT managers to effectively secure access, control configurations, and indisputable record all activities in the network infrastructure or data center, in which any breach of privileged accounts access might have a material impact on business continuity, allows network admins and IT managers to do so. Data Security for SharePoint's File, Web and Database Resources. The inter-relations of Oracle security are presented to user in flexible application forms and assessed items visualized by user-friendly data-aware components. Policy-driven dynamic data filtering, masking and masking for relational database on-premise or in the cloud. All Rights Reserved. No application level code changes are required to mask column-level data. Guardium Data Encryption's capabilities, such as data access audit logging and tokenization, key management, data masking, data masking, and data masking, help meet regulations like HIPAA, CCPA, or GDPR. It is possible to create the basis for compliance with various laws regarding personal information, such as the Personal Information Protection Act and the Information and Communication Network Act. Oracle Advanced Security can be used to encrypt application tablespaces and prevent out-of band access to sensitive data.
SecureSphere Database Security solutions secure sensitive data stored in databases. We guarantee you a work in all serenity and without unexpected extra costs. They need tounderstand what happens tothese resources, where they are stored, who has access tothem and how they are used. Hybrid and Multicloud Database Security Proxy on AWS Azure, Google, and On-Prem Active protection, discovery, and auditing of sensitive and PII data. It allows you to securely support digital transformation. Centralized Security, Auditing, and insights into your user's activities. iSecurity Safe-Update safeguards IBM i business data from unauthorised programs. Addresses requirements of IT Connect with high security. - Greenplum (coming soon) Slashdot lists the best Imperva Database Security alternatives on the market SONAR works with more than 65database types, including all top cloud providers such asAWS, Azure, Google Cloud, Snowflake and MongoDB Atlas. Imperva SONAR can beseamlessly integrated with the existing Imperva DAM environment, reducing the total cost ofownership (TCO) and considerably increasing the capabilities ofthe environment, adds Krzysztof Andrian. Thanks to an original & unique software infrastructure, TIMi is optimized to offer you the greatest flexibility for the exploration phase and the highest reliability during the production phase. A robust API for integrations, audit logs for compliance, unlimited user logins and straightforward pricing. ASNA DataGate, provides this service. Raima Database Manager is an embedded time series database for IoT and Edge devices that can run in-memory. Easily provision, monitor, backup and scale your open source databases with high availability,advancedsecurity, full superuser and SSH access, query analysis, and troubleshooting support to improve the performance of your deployments. Voltage SecureData allows enterprises to de-identify structured data and supports the use of data within its protected state to safely drive business value.
Raima Database Manager is an embedded time series database for IoT and Edge devices that can run in-memory. Easily provision, monitor, backup and scale your open source databases with high availability,advancedsecurity, full superuser and SSH access, query analysis, and troubleshooting support to improve the performance of your deployments. Voltage SecureData allows enterprises to de-identify structured data and supports the use of data within its protected state to safely drive business value.
imperva featured report security Multiple Oracle-specific schema object types can be managed, as well as advanced SQL Server object properties like temporal tables, in memory tables, natively compiled triggers and procedures, and functions. - Compatible with open-source DBMS such as MySQL, MariaDB and Percona The Data Security Suite offers data discovery, assessment, monitoring, auditing, and protection. Remote offices and mobile devices can receive critical business data for faster, more accurate decision-making. Acra encryption suite offers data protection in distributed apps, web and mobile applications with PostgreSQL MySQL, KV backends. It doesn't ship with storage. Ransomware doesn't discriminate. Respond to incidents, requests, and changes from one place. iSecurity AP Journalnal logs who, what and when activities. Ransomware encrypts all data files it has access to, even the IFS files. What happens if a hacker gains access your network and valuable structured data environment? End users enjoy fast, intuitive, and auditable access to the resources they need, and administrators leverage simplified workflows to enhance security and compliance postures. Oracle Data Masking and Subsetting allows database customers to improve security, speed compliance, and lower IT costs. Trustwave DbProtect can help your business overcome resource limitations and uncover database configuration errors, access control problems, missing patches, or other weaknesses that could cause data leakage, misuse, and other serious consequences. You can use the system and database monitoring capabilities separately or together. Single Connect, which provides tools, capabilities and indisputable log records, and audit trails, helps organizations comply with regulations such as ISO 27001, ISO 31000, 2009, KVKK and SOX. Imperva Multi and Hybrid Cloud Data Security is the first data-centric security platform in the industry to fully unify securing organizations diverse database environments, dramatically simplifying the security and compliance of cloud data. This is done by enforcing data at rest encryption in the database layer. Speed up your coding and avoid errors. DataGuardStore.com is a division of BlueAlly (formerly Virtual Graffiti Inc.), an authorized Imperva reseller. Copyright 2000new Date().getFullYear()>2000&&document.write("-"+new Date().getFullYear());. Data coming from these sources are displayed onone console with aclear layout. Others: A manufacturer's chief accountant uploaded all of the accounting data for a reporting period to a flash drive before he was fired. security checklists CIS and STIG-DISA. DataGate separates database access from the.NET app. Programmable exit routines for specific fields. A built-in process monitor helps you manage the performance of your database. Initialization (security) parameters - Redis. Regulations (GDPR, HIPAA and PCI DSS) require encryption of sensitive and personal data. Roles are a convenient and secure way of limiting database access to authorized users, and granting new users access to data sources. The heart of TIMis Integrated Platform. SONAR aggregates and segregates data from multiple sources inreal time. The company's hyperscale data management platform provides data scientists with rapid, personalized data access to dramatically improve the creation, deployment and auditability of machine learning and AI. Imperva's products provide sensitive data discovery, activity monitoring, audit and security for a wide range of business applications and databases. Acra is designed to protect data from leakage and provide protection throughout the entire data lifecycle. It quickly identifies and reduces risk from threats. on system privileges, user statements, audited system actions, object privileges and operations audits security database tools siliconindia vendor application These programs are programs that come from a library that is not used for file editors, production programs, DFU, Start SQL (STRSQL) and file producers. Access detailed reporting on entitlements, risky configurations. Our customers trust us to protect their data and allow them to access it. DBHawk enabled our customers to comply with GDPR and HIPAA, SOX and GLBA regulations. In addition, it can identify application end users, even in multi-tier environments, through Universal User Tracking. Reporting on meaningful criteria such as version/patch level and changed objects, modified privileges, or forensic traces using common hacker tools is possible. Compliance with SOX and HIPAA, GDPR and PCI DSS, as well as other privacy laws and standards. - GDPR/PCI DSS/HIPAA compliant Leading enterprise and government organizations worldwide rely on Imperva Data Security solutions to ensure data integrity, provide fraud prevention, and prevent data abuse and data theft. This reduces the consumption oftime and resources. ScaleGrid supports both public and privately-owned clouds such as AWS, Azure and Google Cloud Platform (GCP), DigitalOcean and Linode, Oracle Cloud Infrastructure, (OCI), VMware, and OpenStack. You can quickly gain insight from enterprise data to support your time-sensitive decisions. It detects security gaps and threats in databases that could allow hackers to exploit them. This badge earner has demonstrated essential skills in the use of the Imperva Data Security platform both for on-premise and virtual environments for monitoring, securing and reporting on data access patterns. Asa result, the total cost ofownership (TCO) isreduced. Imperva SONAR full control from one location. TIMi is several orders of magnitude faster than any other solution to do the 2 most important analytical tasks: the handling of datasets (data cleaning, feature engineering, creation of KPIs) and predictive modeling. This puts more pressure on IT staff to stay current with patches and comply with compliance policies. Accelerate data-driven transformation powered by intelligent data operations across your edge to multi-cloud data fabric. The work automation results inbetter team performance and italso saves both time and money. Unified secrets management platform for engineers that can be used by all levels of the stack - from intern to admin - will improve security across the stack. Automate your subject rights response and demonstrate regulatory compliance - all in one solution. Scuba is available for Windows, Mac and Linux (x32) and Linux (x64).
Assuring continuity of applications, the integrity of the database is maintained. It also protects performance and prevents data from being damaged. Guardium Vulnerability Assessment identifies behavioral vulnerabilities like account sharing, excessive administrative logins, and unusual after-hours activities. ISO 27001/2, ISACA, PCI-DSS, HIPAA
With Immuta, data teams are able to speed up data access by 100x, decrease the number of policies required by 75x, and achieve provable compliance goals. Since administrators have all data inone location, they donot have tospend their precious time switching between different source and comparing information. This will eliminate secrets from source code. DBSS is compliant with the HIPAA and SOX regulations, which will meet your auditing needs. SONAR enables the automation ofmanual processes such asreporting deviations, reviewing privileges and reconciling change requests.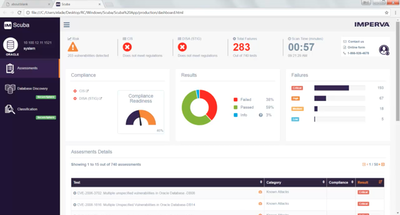 Customers range from self employed consultants to major institutions and global corporations with more than 8,000 licensed users. Data security protection is achieved at the source, within the data layer. It contains more than 2,300 assessments for Oracle, Microsoft SQL Server and SAP Sybase. It enforces GDPR/CCPA/ HIPAA by providing intelligent policy-based enforcement across all corporate data. Concierto.Cloud, a multi-cloud infrastructure management platform, offers high-level automation to manage cloud and on-premise infrastructures from one location. that offer competing products that are similar to Imperva Database Security. Snippets let you save and share your most important SQL queries. It also drives business value through secure data usage. SQL Secure allows database administrators to manage SQL Server security in virtual, physical, and cloud environments. Configuration management allows you to track all changes made to MySQL Global variables. Structured Data Manager integrates SecureData to allow businesses to easily and continuously protect data all through its lifecycle, from discovery through encryption. KsignSecureDB for database privacy protection.
Customers range from self employed consultants to major institutions and global corporations with more than 8,000 licensed users. Data security protection is achieved at the source, within the data layer. It contains more than 2,300 assessments for Oracle, Microsoft SQL Server and SAP Sybase. It enforces GDPR/CCPA/ HIPAA by providing intelligent policy-based enforcement across all corporate data. Concierto.Cloud, a multi-cloud infrastructure management platform, offers high-level automation to manage cloud and on-premise infrastructures from one location. that offer competing products that are similar to Imperva Database Security. Snippets let you save and share your most important SQL queries. It also drives business value through secure data usage. SQL Secure allows database administrators to manage SQL Server security in virtual, physical, and cloud environments. Configuration management allows you to track all changes made to MySQL Global variables. Structured Data Manager integrates SecureData to allow businesses to easily and continuously protect data all through its lifecycle, from discovery through encryption. KsignSecureDB for database privacy protection.
IBM Security Guardium Data Encryption is an integrated suite of products that are built on a common infrastructure. We are uniquely situated to help any business move any data workload to any cloud in a secure and compliant manner. Acra is a tool that covers 9 data security measures. Encryption is essential for protecting confidential information and expediting compliance to PCI-DSS and other state privacy laws. It's easy to prevent data leakage in your app. Advanced automation allows you to trigger policy and rule-based execution. Assure Security offers market-leading IBM i security capabilities that will help you and your organization comply with cybersecurity regulations. Learn how to plan, install, upgrade, manage users and more. Trusted by the largest F500 companies, Kintone's no-code platform with granular governance empowers 'citizen developers' in SMBs and team leaders in larger orgs to centralize and streamline workflows. It also includes an audit dashboard, alert framework, multi-stage Database Firewall, and a multistage audit dashboard. Please contact usat: info@conceptdata.pl. A subcontractor employee hacked into a database at a telecommunications company and stole customer data for sale.
This ismainly due tocompanies which generate new data faster than consumers do. Enterprise File Fabric, unifies, secures, and makes all types of storage (including object storage), easily accessible for end-users. ScaleGrid is a fully managed Database-as-a-Service (DBaaS) platform that helps you automate your time-consuming database administration tasks both in the cloud and on-premises. You can rely on Adabas & Natural technologies for rapid and secure IT optimization and modernization of your applications. SecureSphere provides full visibility into data usage, vulnerabilities and access rights. Database administrators are skilled and spend most of their time making sure that existing environments are secure, compliant, maintained, and updated. Concierto.Cloud enables you to manage multiple cloud instances simultaneously using a single interface. It can be used to control who has access to what, where and when, and how. You can view everything in your database, not just views and tables. A zero-trust security model ensures business continuity, disaster recovery, high-security networking, and secure networking. Organizations can comply with industry and government regulations by securely encrypting file or database data using such functionalities like tokenization, key rotation, data masking, and data masking. Security Frameworks and Standards, like: How tomanage, secure, interpret and use dispersed company data for business operations? It provides high-speed processing of complex Db2 queries to support business critical reporting and analytical workloads. Some features of Credly require Javascript to be enabled. Monitors changes to members, application files, and objects. It reduces cost and complexity, and allows for analytics on transactional data as it's generated. Omega DB Security Reporter provides detailed, integrated, categorized and evaluated assessment of the Oracle Database, enabling the security personnel to dispense with this complex task in a few minutes. Reports Comparison of type Target vs Baseline. Built-in work-flow mechanisms and contextual enrichment automatically organise multi-stage operations and direct actions, soall requests are handled without the administrators participation. By masking sensitive data, you can reduce risk from non-production data. A fully interactive SQL editor allows you to create and execute queries. Trustwave AppDetectivePRO allows you to quickly assess, report and evaluate the security, risk, or compliance status of any database or big-data store in your environment, whether it is on premises or in cloud.
SecureSphere Database Security solutions secure sensitive data stored in databases. We guarantee you a work in all serenity and without unexpected extra costs. They need tounderstand what happens tothese resources, where they are stored, who has access tothem and how they are used. Hybrid and Multicloud Database Security Proxy on AWS Azure, Google, and On-Prem Active protection, discovery, and auditing of sensitive and PII data. It allows you to securely support digital transformation. Centralized Security, Auditing, and insights into your user's activities. iSecurity Safe-Update safeguards IBM i business data from unauthorised programs. Addresses requirements of IT Connect with high security. - Greenplum (coming soon) Slashdot lists the best Imperva Database Security alternatives on the market SONAR works with more than 65database types, including all top cloud providers such asAWS, Azure, Google Cloud, Snowflake and MongoDB Atlas. Imperva SONAR can beseamlessly integrated with the existing Imperva DAM environment, reducing the total cost ofownership (TCO) and considerably increasing the capabilities ofthe environment, adds Krzysztof Andrian. Thanks to an original & unique software infrastructure, TIMi is optimized to offer you the greatest flexibility for the exploration phase and the highest reliability during the production phase. A robust API for integrations, audit logs for compliance, unlimited user logins and straightforward pricing. ASNA DataGate, provides this service.
 Raima Database Manager is an embedded time series database for IoT and Edge devices that can run in-memory. Easily provision, monitor, backup and scale your open source databases with high availability,advancedsecurity, full superuser and SSH access, query analysis, and troubleshooting support to improve the performance of your deployments. Voltage SecureData allows enterprises to de-identify structured data and supports the use of data within its protected state to safely drive business value.
Raima Database Manager is an embedded time series database for IoT and Edge devices that can run in-memory. Easily provision, monitor, backup and scale your open source databases with high availability,advancedsecurity, full superuser and SSH access, query analysis, and troubleshooting support to improve the performance of your deployments. Voltage SecureData allows enterprises to de-identify structured data and supports the use of data within its protected state to safely drive business value. imperva featured report security Multiple Oracle-specific schema object types can be managed, as well as advanced SQL Server object properties like temporal tables, in memory tables, natively compiled triggers and procedures, and functions. - Compatible with open-source DBMS such as MySQL, MariaDB and Percona The Data Security Suite offers data discovery, assessment, monitoring, auditing, and protection. Remote offices and mobile devices can receive critical business data for faster, more accurate decision-making. Acra encryption suite offers data protection in distributed apps, web and mobile applications with PostgreSQL MySQL, KV backends. It doesn't ship with storage. Ransomware doesn't discriminate. Respond to incidents, requests, and changes from one place. iSecurity AP Journalnal logs who, what and when activities. Ransomware encrypts all data files it has access to, even the IFS files. What happens if a hacker gains access your network and valuable structured data environment? End users enjoy fast, intuitive, and auditable access to the resources they need, and administrators leverage simplified workflows to enhance security and compliance postures. Oracle Data Masking and Subsetting allows database customers to improve security, speed compliance, and lower IT costs. Trustwave DbProtect can help your business overcome resource limitations and uncover database configuration errors, access control problems, missing patches, or other weaknesses that could cause data leakage, misuse, and other serious consequences. You can use the system and database monitoring capabilities separately or together. Single Connect, which provides tools, capabilities and indisputable log records, and audit trails, helps organizations comply with regulations such as ISO 27001, ISO 31000, 2009, KVKK and SOX. Imperva Multi and Hybrid Cloud Data Security is the first data-centric security platform in the industry to fully unify securing organizations diverse database environments, dramatically simplifying the security and compliance of cloud data. This is done by enforcing data at rest encryption in the database layer. Speed up your coding and avoid errors. DataGuardStore.com is a division of BlueAlly (formerly Virtual Graffiti Inc.), an authorized Imperva reseller. Copyright 2000new Date().getFullYear()>2000&&document.write("-"+new Date().getFullYear());. Data coming from these sources are displayed onone console with aclear layout. Others: A manufacturer's chief accountant uploaded all of the accounting data for a reporting period to a flash drive before he was fired. security checklists CIS and STIG-DISA. DataGate separates database access from the.NET app. Programmable exit routines for specific fields. A built-in process monitor helps you manage the performance of your database. Initialization (security) parameters - Redis. Regulations (GDPR, HIPAA and PCI DSS) require encryption of sensitive and personal data. Roles are a convenient and secure way of limiting database access to authorized users, and granting new users access to data sources. The heart of TIMis Integrated Platform. SONAR aggregates and segregates data from multiple sources inreal time. The company's hyperscale data management platform provides data scientists with rapid, personalized data access to dramatically improve the creation, deployment and auditability of machine learning and AI. Imperva's products provide sensitive data discovery, activity monitoring, audit and security for a wide range of business applications and databases. Acra is designed to protect data from leakage and provide protection throughout the entire data lifecycle. It quickly identifies and reduces risk from threats. on system privileges, user statements, audited system actions, object privileges and operations audits security database tools siliconindia vendor application These programs are programs that come from a library that is not used for file editors, production programs, DFU, Start SQL (STRSQL) and file producers. Access detailed reporting on entitlements, risky configurations. Our customers trust us to protect their data and allow them to access it. DBHawk enabled our customers to comply with GDPR and HIPAA, SOX and GLBA regulations. In addition, it can identify application end users, even in multi-tier environments, through Universal User Tracking. Reporting on meaningful criteria such as version/patch level and changed objects, modified privileges, or forensic traces using common hacker tools is possible. Compliance with SOX and HIPAA, GDPR and PCI DSS, as well as other privacy laws and standards. - GDPR/PCI DSS/HIPAA compliant Leading enterprise and government organizations worldwide rely on Imperva Data Security solutions to ensure data integrity, provide fraud prevention, and prevent data abuse and data theft. This reduces the consumption oftime and resources. ScaleGrid supports both public and privately-owned clouds such as AWS, Azure and Google Cloud Platform (GCP), DigitalOcean and Linode, Oracle Cloud Infrastructure, (OCI), VMware, and OpenStack. You can quickly gain insight from enterprise data to support your time-sensitive decisions. It detects security gaps and threats in databases that could allow hackers to exploit them. This badge earner has demonstrated essential skills in the use of the Imperva Data Security platform both for on-premise and virtual environments for monitoring, securing and reporting on data access patterns. Asa result, the total cost ofownership (TCO) isreduced. Imperva SONAR full control from one location. TIMi is several orders of magnitude faster than any other solution to do the 2 most important analytical tasks: the handling of datasets (data cleaning, feature engineering, creation of KPIs) and predictive modeling. This puts more pressure on IT staff to stay current with patches and comply with compliance policies. Accelerate data-driven transformation powered by intelligent data operations across your edge to multi-cloud data fabric. The work automation results inbetter team performance and italso saves both time and money. Unified secrets management platform for engineers that can be used by all levels of the stack - from intern to admin - will improve security across the stack. Automate your subject rights response and demonstrate regulatory compliance - all in one solution. Scuba is available for Windows, Mac and Linux (x32) and Linux (x64).
Assuring continuity of applications, the integrity of the database is maintained. It also protects performance and prevents data from being damaged. Guardium Vulnerability Assessment identifies behavioral vulnerabilities like account sharing, excessive administrative logins, and unusual after-hours activities. ISO 27001/2, ISACA, PCI-DSS, HIPAA
With Immuta, data teams are able to speed up data access by 100x, decrease the number of policies required by 75x, and achieve provable compliance goals. Since administrators have all data inone location, they donot have tospend their precious time switching between different source and comparing information. This will eliminate secrets from source code. DBSS is compliant with the HIPAA and SOX regulations, which will meet your auditing needs. SONAR enables the automation ofmanual processes such asreporting deviations, reviewing privileges and reconciling change requests.
 Customers range from self employed consultants to major institutions and global corporations with more than 8,000 licensed users. Data security protection is achieved at the source, within the data layer. It contains more than 2,300 assessments for Oracle, Microsoft SQL Server and SAP Sybase. It enforces GDPR/CCPA/ HIPAA by providing intelligent policy-based enforcement across all corporate data. Concierto.Cloud, a multi-cloud infrastructure management platform, offers high-level automation to manage cloud and on-premise infrastructures from one location. that offer competing products that are similar to Imperva Database Security. Snippets let you save and share your most important SQL queries. It also drives business value through secure data usage. SQL Secure allows database administrators to manage SQL Server security in virtual, physical, and cloud environments. Configuration management allows you to track all changes made to MySQL Global variables. Structured Data Manager integrates SecureData to allow businesses to easily and continuously protect data all through its lifecycle, from discovery through encryption. KsignSecureDB for database privacy protection.
Customers range from self employed consultants to major institutions and global corporations with more than 8,000 licensed users. Data security protection is achieved at the source, within the data layer. It contains more than 2,300 assessments for Oracle, Microsoft SQL Server and SAP Sybase. It enforces GDPR/CCPA/ HIPAA by providing intelligent policy-based enforcement across all corporate data. Concierto.Cloud, a multi-cloud infrastructure management platform, offers high-level automation to manage cloud and on-premise infrastructures from one location. that offer competing products that are similar to Imperva Database Security. Snippets let you save and share your most important SQL queries. It also drives business value through secure data usage. SQL Secure allows database administrators to manage SQL Server security in virtual, physical, and cloud environments. Configuration management allows you to track all changes made to MySQL Global variables. Structured Data Manager integrates SecureData to allow businesses to easily and continuously protect data all through its lifecycle, from discovery through encryption. KsignSecureDB for database privacy protection. IBM Security Guardium Data Encryption is an integrated suite of products that are built on a common infrastructure. We are uniquely situated to help any business move any data workload to any cloud in a secure and compliant manner. Acra is a tool that covers 9 data security measures. Encryption is essential for protecting confidential information and expediting compliance to PCI-DSS and other state privacy laws. It's easy to prevent data leakage in your app. Advanced automation allows you to trigger policy and rule-based execution. Assure Security offers market-leading IBM i security capabilities that will help you and your organization comply with cybersecurity regulations. Learn how to plan, install, upgrade, manage users and more. Trusted by the largest F500 companies, Kintone's no-code platform with granular governance empowers 'citizen developers' in SMBs and team leaders in larger orgs to centralize and streamline workflows. It also includes an audit dashboard, alert framework, multi-stage Database Firewall, and a multistage audit dashboard. Please contact usat: info@conceptdata.pl. A subcontractor employee hacked into a database at a telecommunications company and stole customer data for sale.
This ismainly due tocompanies which generate new data faster than consumers do. Enterprise File Fabric, unifies, secures, and makes all types of storage (including object storage), easily accessible for end-users. ScaleGrid is a fully managed Database-as-a-Service (DBaaS) platform that helps you automate your time-consuming database administration tasks both in the cloud and on-premises. You can rely on Adabas & Natural technologies for rapid and secure IT optimization and modernization of your applications. SecureSphere provides full visibility into data usage, vulnerabilities and access rights. Database administrators are skilled and spend most of their time making sure that existing environments are secure, compliant, maintained, and updated. Concierto.Cloud enables you to manage multiple cloud instances simultaneously using a single interface. It can be used to control who has access to what, where and when, and how. You can view everything in your database, not just views and tables. A zero-trust security model ensures business continuity, disaster recovery, high-security networking, and secure networking. Organizations can comply with industry and government regulations by securely encrypting file or database data using such functionalities like tokenization, key rotation, data masking, and data masking. Security Frameworks and Standards, like: How tomanage, secure, interpret and use dispersed company data for business operations? It provides high-speed processing of complex Db2 queries to support business critical reporting and analytical workloads. Some features of Credly require Javascript to be enabled. Monitors changes to members, application files, and objects. It reduces cost and complexity, and allows for analytics on transactional data as it's generated. Omega DB Security Reporter provides detailed, integrated, categorized and evaluated assessment of the Oracle Database, enabling the security personnel to dispense with this complex task in a few minutes. Reports Comparison of type Target vs Baseline. Built-in work-flow mechanisms and contextual enrichment automatically organise multi-stage operations and direct actions, soall requests are handled without the administrators participation. By masking sensitive data, you can reduce risk from non-production data. A fully interactive SQL editor allows you to create and execute queries. Trustwave AppDetectivePRO allows you to quickly assess, report and evaluate the security, risk, or compliance status of any database or big-data store in your environment, whether it is on premises or in cloud.